L3 Segmentation vs L2 VLANs
Introduction
Since the introduction of VLANs (802.1q), networks have become increasingly complex. Cloud adoption, IoT proliferation, and heightened security needs have exposed the limitations of traditional Layer 2 segmentation approaches.
Broadcast domain limitations, complex management overhead, and insufficient security boundaries hinder scalability, agility, and the ability to enforce granular access controls.
This document explores how dynamic, policy driven Layer 3 segmentation, a foundational innovation of the Nile Access Service (NaaS), addresses these challenges, enabling organizations to build secure, dynamic, and future-proof networks.
What is Layer 3 Segmentation?
Layer 3 segmentation, also known as network virtualization or overlay networks, is an approach to logically dividing a network into secure, isolated segments at the network layer (Layer 3) of the OSI model. It leverages virtualization technologies and routing protocols to create logical subnets that can span across multiple physical networks and locations.
Unlike traditional VLANs, which operate at the data link layer (Layer 2) and are confined to broadcast domains, Layer 3 segmentation transcends these limitations by separating the logical network topology from the underlying physical infrastructure. This separation enables greater flexibility, scalability, and enhanced security compared to VLAN-based segmentation methods.
Key advantages of Layer 3 segmentation include:
- Scalability: Layer 3 segmentation can accommodate a large number of logical segments without the limitations of broadcast domains or VLAN ID exhaustion, making it suitable for large-scale deployments and cloud environments.
- Security: By default, each segment, device and user is logically isolated from others, mitigating the spread of threats and reducing the attack surface. This aligns with our principles of zero-trust architectures and microsegmentation.
- Flexibility: Logical segments can be created, modified, or removed dynamically, independent of the underlying physical network infrastructure, enabling agile and responsive network management.
- Centralized Management: Layer 3 segmentation by Nile delivers centralized management and policy enforcement, simplifying the configuration and administration of network segmentation across distributed environments.
- Location Independence: Network access and connectivity are no longer tied to physical locations or switch ports. Instead, users and devices can be assigned to logical segments based on policies, identities, or application requirements, enabling secure access from anywhere.
Layer 3 segmentation operates at the network layer by leveraging routing protocols, such as OSPF or BGP, to facilitate communication between segments. Each segment functions as a separate logical subnet or virtual network, with routing mechanisms handling inter-segment traffic.
This approach enables organizations to implement granular access controls, microsegmentation, and continuous authentication and authorization, aligning with the principles of zero-trust architectures and enhancing overall network security posture
Layer 2 vs Layer 3
| Characteristic | VLAN (Layer 2) | Layer 3 Segmentation |
|---|---|---|
| Scope of Segmentation | Confined to the broadcast domain | Creates logical subnets isolated at the network layer |
| Role of Routing | Requires external routers for inter-VLAN communication | Inherently leverages routing for inter-segment traffic |
| Configuration Complexity | Accelerating configuration overhead across multiple devices and vendors | Centralized configuration enabling granular, policy-based enforcement aligned with zero-trust principles |
| Security Vulnerabilities | Susceptible to attacks within shared broadcast domains and at the physical port layer. |
Default isolation between segments, users and devices, mitigating the spread of threats |
| Redundant Connectivity | Implementing redundant links is cumbersome | OSPF routing enables optimized path selection |
| Broadcast Domain Issues | Prone to broadcast storms and performance degradation in large networks | Significantly reduces broadcast traffic, enhancing performance |
| Connectivity Approach | Often tied to physical location or switch port | Enables policy-based connectivity based on user identity, device type, or application |
The dynamic Layer 3 segmentation provided by the Nile Access Service, provides a robust foundation for implementing zero-trust architectures. This is due to its ability to enable granular network microsegmentation, policy-driven access controls, and continuous authentication and authorization.
Why Layer 3 Segmentation?
Policy driven vs location driven connectivity; no matter where a user or device connects they will be connected to their assigned Segment. Dynamic segmentation can be driven by device fingerprinting and NBAC.
Zero trust wired access; No more Access port vulnerabilities. Disconnecting a printer and plugging into that port does not grant access to the network.
Overview Deck - Slide 7
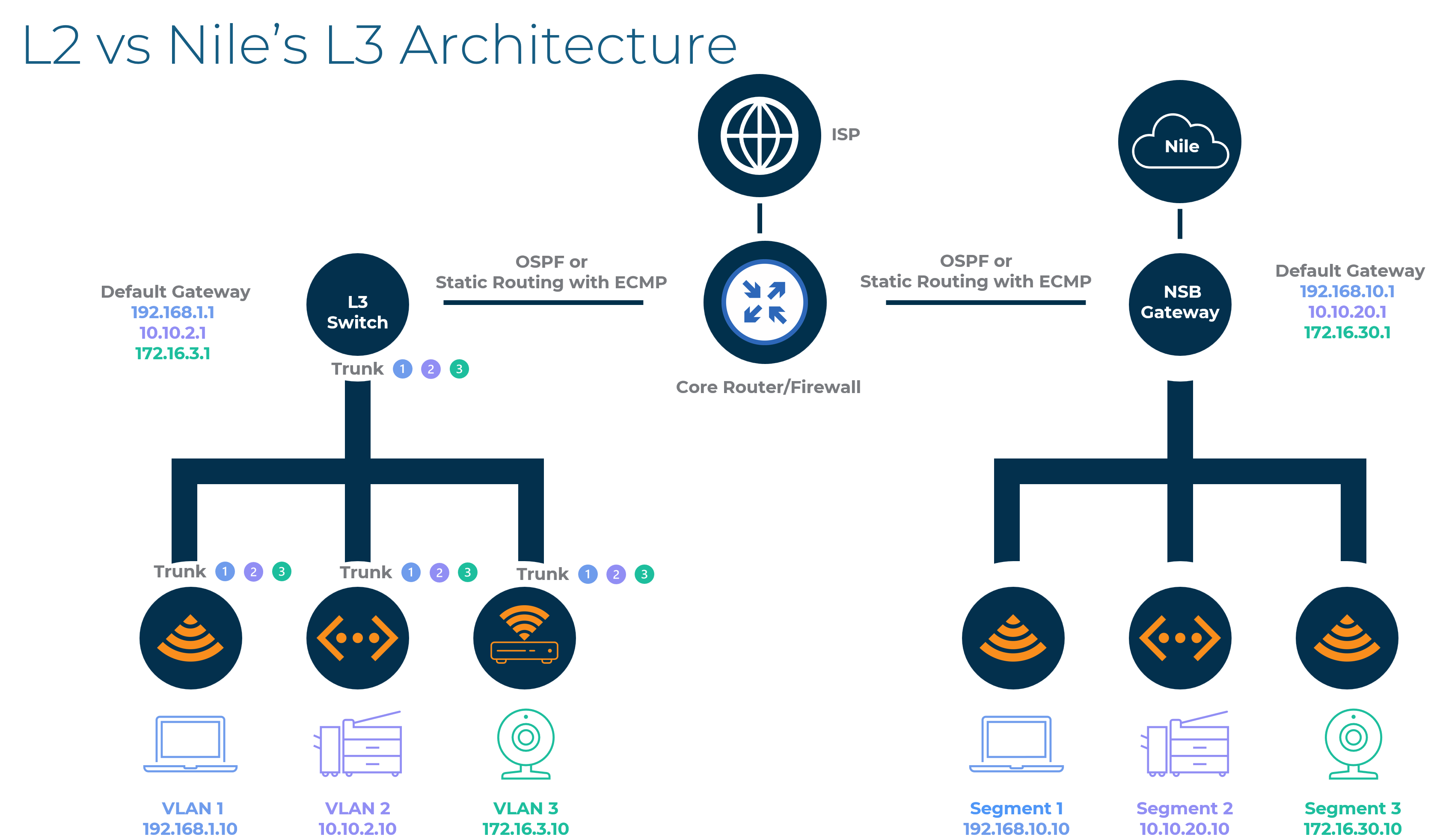
Let's dive a bit deeper into the architecture and see how does a traditional L2 network compare to Nile’s L3 architecture. Take a 3-tier architecture for example. We have an access layer which connects to a distribution layer which in turn connects to a core routing layer. C1 All devices are assigned to a VLAN. Hence the admin needs to define these VLANs in the distribution and access layer.
C2 - If using an independent Acesss Point we need to trunk the AP’s ethernet port with all the VLANs. If it’s a wired switch then each port needs be configured with a VLAN and the uplink with a trunk. If it is a wireless controller, then the uplink port has to be trunked. Anytime a new VLAN is introduced, the admin has to configure the entire stack. This is time consuming and error prone.
C3 - Between the L3 switch and router OSPF can be leveraged to distribute the routes.
C4 – With Nile’s architecture there is no VLAN’s or trunk required within the NSB.
C5 - Instead of assigning VLAN’s to devices, segments are assigned which are essentially subnets
C6 – The admin defines all the subnets in the Nile portal which pushes these settings to the NSB. The NSB thus becomes the default gateway for all subnets
C7 – The NSB exchanges these routers with the upstream firewall or router to route packets in and out thus eliminating the needs for trunks and VLANS