What is the Nile Access Service?
Legacy network management is complex, reactive, and inhibits security and scalability. Nile Access Service is a cloud-native platform that simplifies connectivity, enforces zero-trust principles, and ensures optimal user experience.
Nile delivers wired and wireless connectivity as a service within a cloud-native platform. In this document, we'll explore the architecture and features of the Nile Access Service, along with its deployment model within modern enterprise networks.
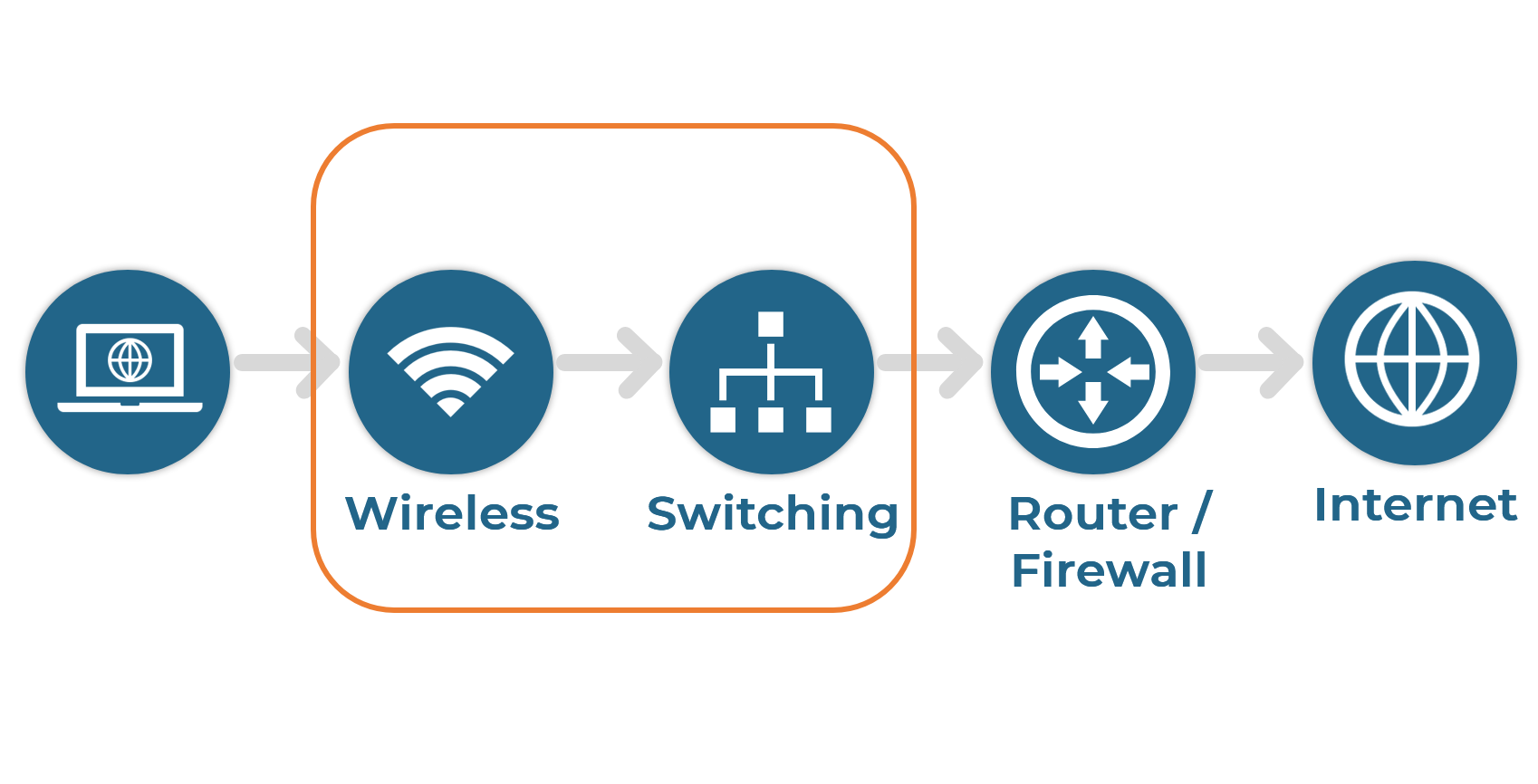
A typical network consists of user and devices connecting via wired or wireless at the access layer. Upstream to the access is the core router and/or firewall which connects to the Internet. Nile focuses on providing Network as a Service for all wired and wireless users and devices.
Nile is not an MSP. We provide connectivity infrastructure in the same way Amazon, Google and Microsoft provide cloud compute. You configure the system to deliver services required, and Nile ensures the underlying infrastructure provides the necessary capacity and reliability.
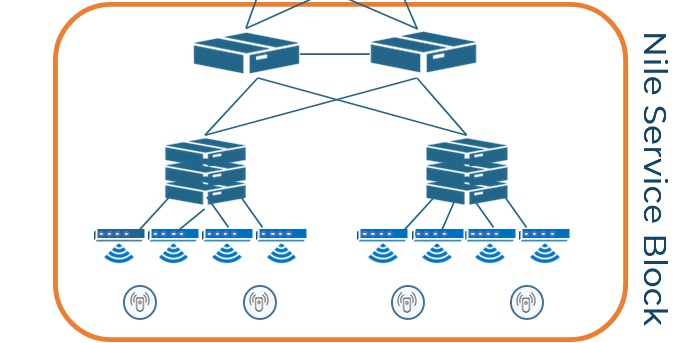
The Nile Access Service is delivered by combining modern cloud architecture with fully integrated hardware. The Nile Service Block (NSB) includes switching, APs and sensors. Which have all been developed in-house, to achieve our goal of bringing an Apple-like experience to the enterprise.
There are a number of notable innovations that support the Nile Access Service;
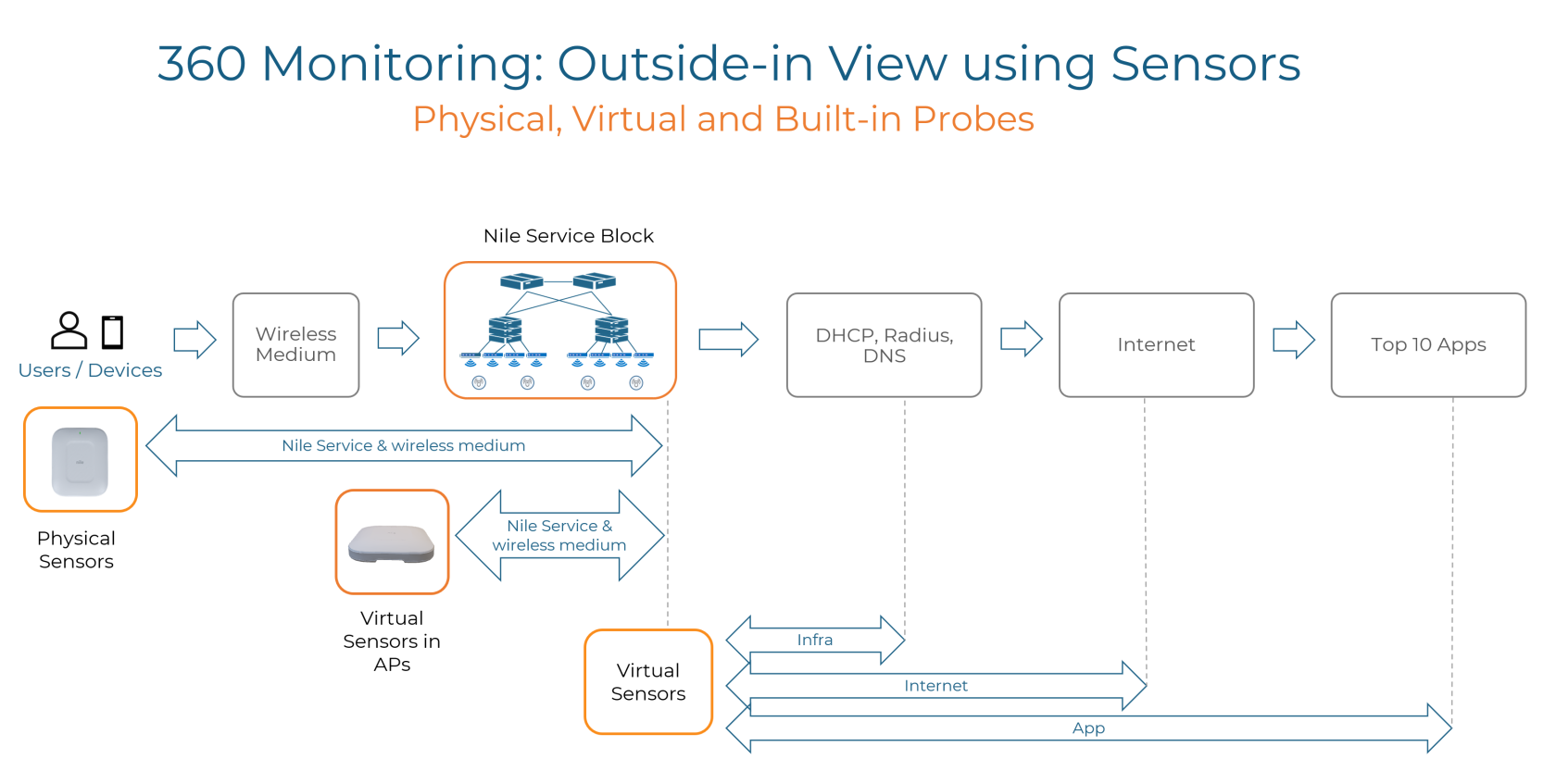
- 'Outside-In' Approach: Nile utilizes physical and virtual sensors for proactive monitoring, ensuring consistent end-user experience and rapid issue resolution.
- Redundancy by Default: Nile's architecture prioritizes redundancy at all layers, minimizing downtime and maintaining service availability even during hardware failures.
- Layer 3, Host-based Segmentation: Nile replaces traditional VLANs with Layer 3 segmentation, enhancing security and simplifying policy management.
- Campus Zero Trust: Nile enforces granular access controls and micro-segmentation based on device identity, minimizing attack surface and lateral movement.
- Shared Responsibility: Nile's cloud-delivered model provides a clear delineation of responsibilities, simplifying operations for IT teams.
Let's explore each of these in more detail.
The 'Outside-In' Approach
Nile simplifies network management and ensures optimal user experience through proactive monitoring. We've deployed an "Outside-In" approach, utilizing wall-mounted physical WiFi sensors, Nile AP dedicated monitoring radio, and a range of virtual sensors throughout the NSB further enhancing our comprehensive data collection.
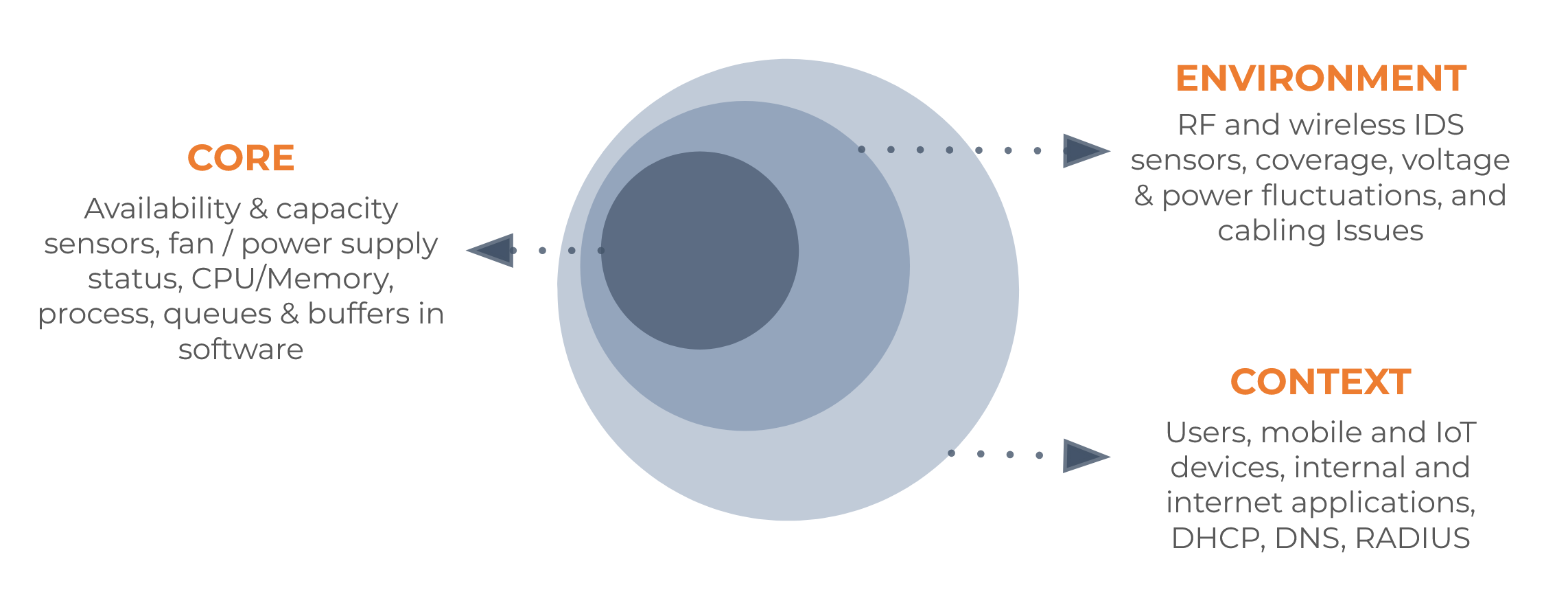
Using these sensors to construct a real-time, outside in view in three key areas; Core, Environment & Context.
Core
The sensors monitoring the Core are continuously monitoring critical services;
- Network Availability: Validates NSB availability to end users and devices
- Coverage: Validating if the sensor can hear at least on AP with -67dm or better signal (Video conferencing quality signal)
- Capacity: Validates if the committed number of AP's on a floor are functioning or not
Designing our own hardware means we can embed physical and virtual sensors through out the NSB in order to gather the deep intelligence required to deliver fully automated infrastructure.
Environment
Ensuring continuous service doesn't end at the NSB, we actively monitor power delivery, data cabling infrastructure, and the RF space for any service affecting issues in the physical Environment where Nile Access Service is deployed.
Context
The main page of the Nile Portal always displays the health of your Top 10 most used applications, DNS, DHCP and authentication services. The usage patterns for both network devices and users are also monitored for anomalous activity. Monitoring the Context of the Nile Access Service using the outside in approach delivers a detailed view of user experience.
This data-driven approach to monitoring Core, Environment, and Context underpins our industry-leading verifiable SLAs. Unlike traditional network monitoring that often relies on user-reported issues, Nile's "Outside-In" method proactively identifies and resolves potential problems before they significantly impact the end-user experience.
Additionally, Nile's reporting tools are a fundamental tool in planning future capacity and coverage with your team.
The Nile network is guaranteed to be always-on and backed financially if SLAs are not met.
Nile SLAs
Nile stands apart from traditional connectivity providers with financially backed SLAs that guarantee network reliability and a 99.5% uptime commitment. This is enabled through the Availability, Coverage, and Capacity monitoring provided by our Outside In approach.
Our proactive monitoring allows us to alert you of potential issues before they significantly impact your users. If a violation of our 99.5% SLA occurs, Nile provides financial credits, demonstrating our commitment to exceptional service. We calculate SLA compliance monthly, per building, based on the percentage of time Nile meets the above thresholds.
[INSERT IMAGE OF SLA REPORT]
[JR: I need to understand core/context in greater detail, and where it should fit in this doc?] Core: Core is basically what Nile offers, Secure Wireless and Wired connectivity as a service. Context: Context is the infrastructure that supports the Nile Access Service, these include the Internet, DHCP, DNS , Radius, device and applications
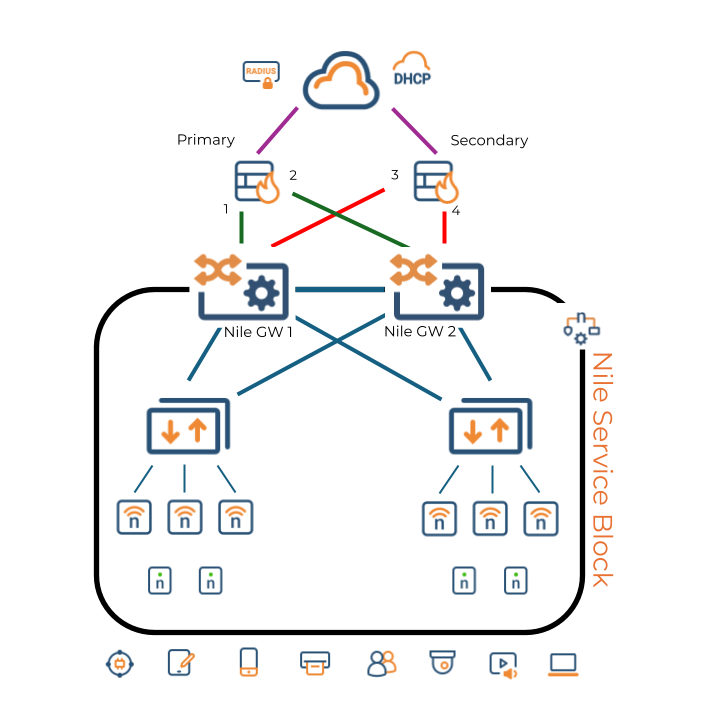
Nile's High-Availability Architecture
Nile's architecture is designed to ensure maximum uptime and minimize service disruptions. We achieve this through built-in redundancy at every layer of the Nile Service Block:
-
NSB Gateway NSB gateway is a role that is assumed by the switch that connects to the customers upstream router/firewall using OSPF to dynamically manage path failover, ensuring continuous connectivity even if a hardware component fails. Whether a large campus with Distribution switches or a remote site with only Access switching, NSB Gateway guarantees service resiliency.
-
Access: Two or more Nile Access switches are deployed per wiring closet, coupled with a "Salt & Pepper" WiFi configuration where neighboring APs are connected to different switches in the wiring closet. Should a switch fail, WiFi coverage remains unaffected, and only a subset of your wired ports on the floor are impacted. Given that the Nile Access Service does not have port level config, affected devices can be easily moved from the impacted Access Switch to a functioning AS. OSPF ensures upstream path redundancy.
This proactive focus on high availability underpins our SLAs and allows IT teams to focus on delivering an exceptional user experience instead of troubleshooting outages.
Learn more about the Nile Service Block.
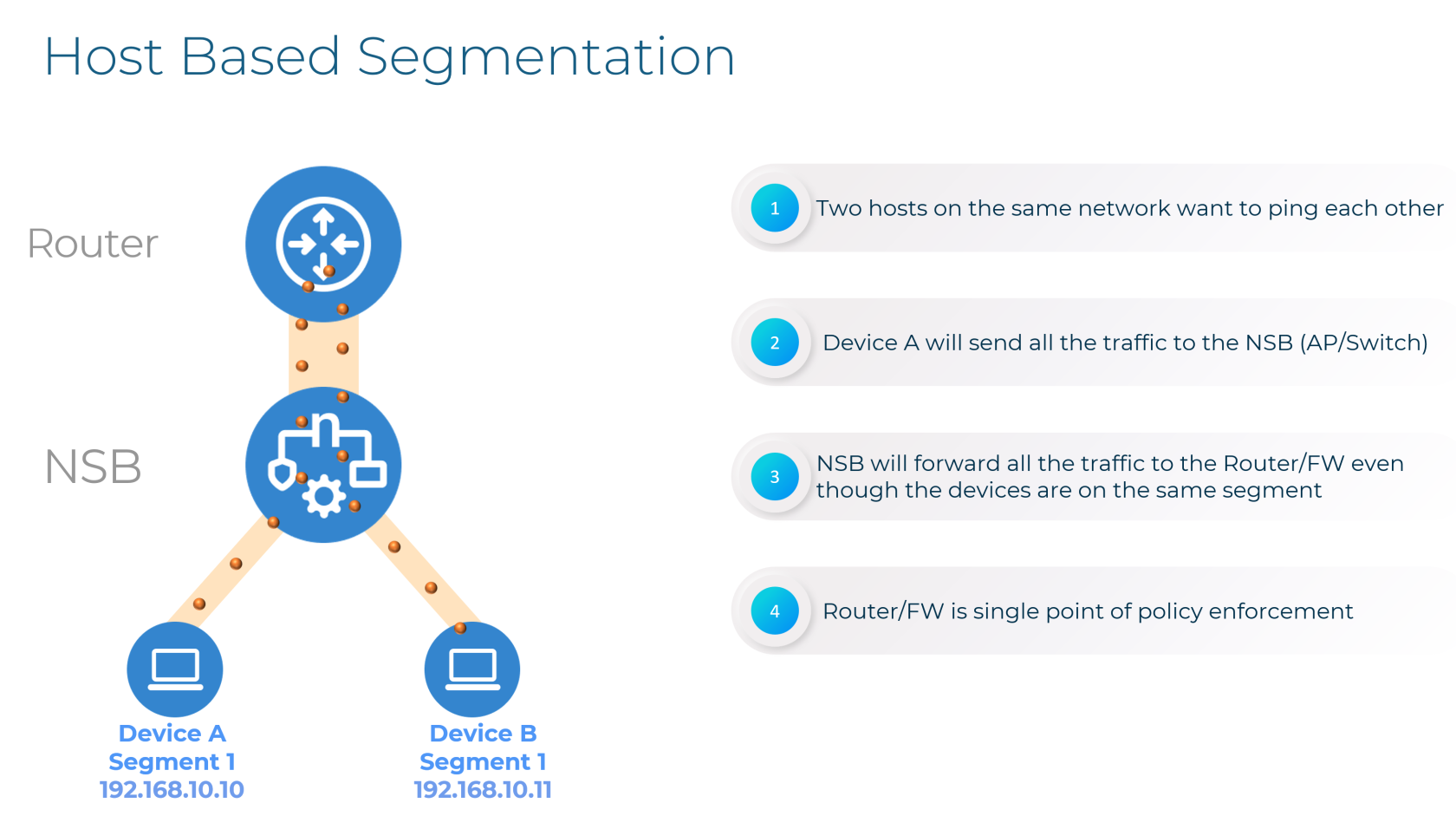
Host-Based Segmentation
Nile simplifies network management and enhances security by replacing traditional VLANs with Layer 3 host-based segmentation. This approach enables granular access control, micro-segmentation, and a streamlined operational model.
-
Flexible Assignment: Nile dynamically assigns segments to devices based on MAC address and device fingerprinting. Unidentified devices can be automatically isolated or placed into a restricted "guest" segment for further review, enhancing security posture.
-
Centralized Policy Enforcement: Nile integrates with security appliances like Fortinet, Palo Alto, and cloud-based services like ZScaler, enabling centralized policy definition and enforcement based on segment membership.
-
Operational Simplicity: With Nile, there's no need to configure VLANs on individual switch ports. Segments are defined and managed globally through Nile's cloud-based platform, significantly reducing configuration complexity.
-
Dynamic Routing: Nile Access Services utilizes OSPF for efficient routing and failover, ensuring network resilience and policy consistency.
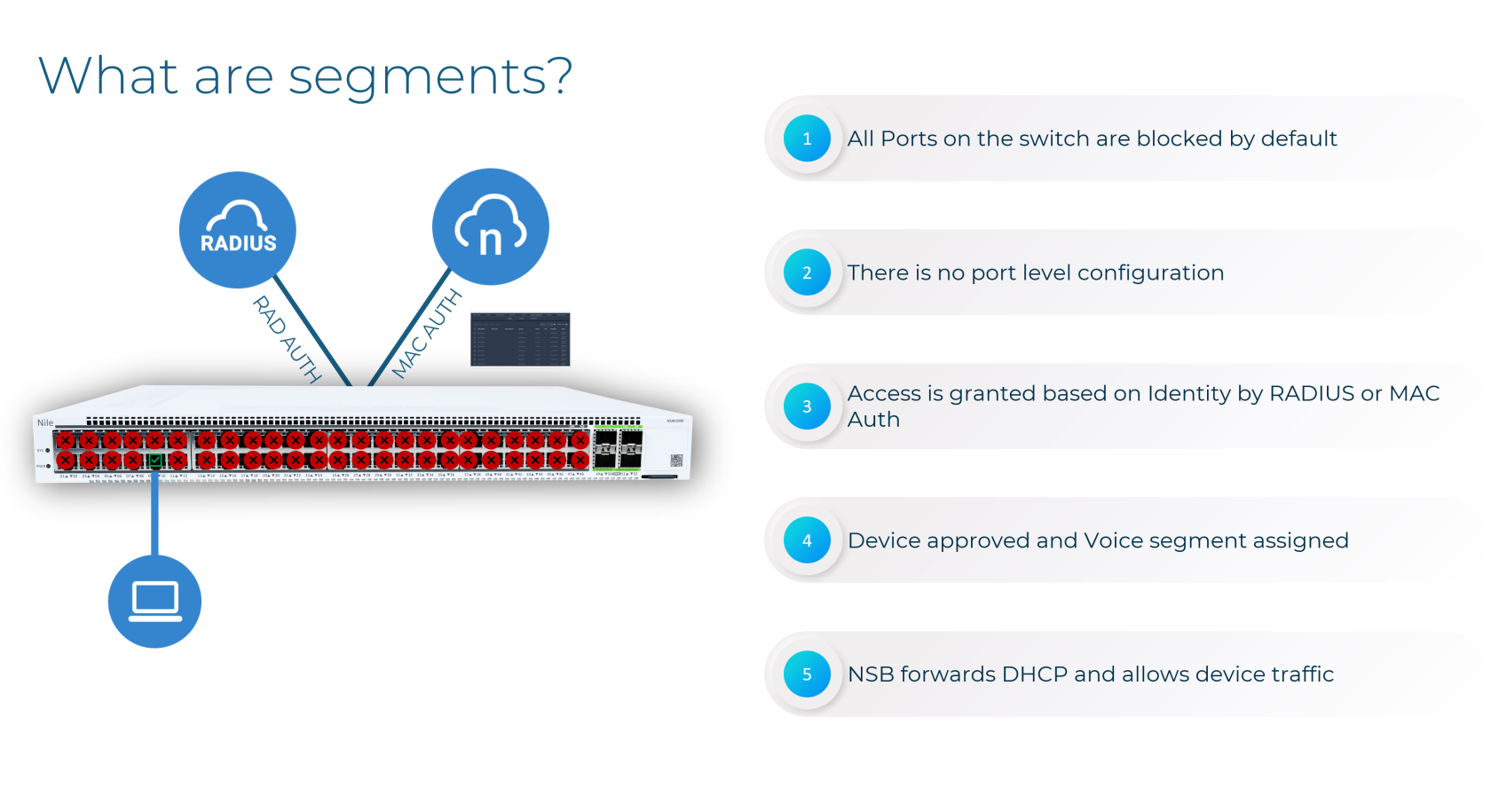 Segments within the Nile Access Service are globally defined, allowing consistent policy enforcement across multiple sites (SFO, BLR, FRA, etc.). This eliminates the need to replicate VLAN configurations on every switch, significantly streamlining network management. The segment-based model aligns with Zero Trust principles, enabling granular access control that follows users and devices regardless of their physical location.
Segments within the Nile Access Service are globally defined, allowing consistent policy enforcement across multiple sites (SFO, BLR, FRA, etc.). This eliminates the need to replicate VLAN configurations on every switch, significantly streamlining network management. The segment-based model aligns with Zero Trust principles, enabling granular access control that follows users and devices regardless of their physical location.
The diagram below illustrates how this works for two devices in the same Layer 3 segment.
RL - > Now we have micro-segmentation available so there is no need to send anything to the upstream device. Should we talk about our micro-segmentation?
If we are going to show the below diagram, we should show a Firewall and not a router as the firewall has policies for allowing/denying the traffic.
Learn more about Nile's host based segmentation.
Campus Zero Trust
Nile's architecture incorporates Zero Trust principles to enhance security and simplify network management. This "never trust, always verify" approach minimizes the attack surface and reduces the risk of unauthorized access or lateral movement within your network.
-
Flexible Authentication: Nile integrates seamlessly with existing NAC solutions and can leverage device fingerprinting and MAC authentication bypass for granular access control. Policies are dynamically assigned based on authentication methods, ensuring the principle of least privilege.
-
Layer 3 Micro-Segmentation: Nile's Layer 3 segmentation isolates users, devices, and applications. This approach goes beyond traditional VLANs to provide enhanced security and flexibility, limiting the potential for lateral movement by attackers.
-
Distributed Policy Enforcement: Access control policies are enforced consistently throughout the Nile Service Block. Nile can integrate with upstream firewalls and security services to dynamically apply policies based on evolving needs and threat conditions.
-
AI-Powered Visibility: Nile's cloud-based reporting and AI-powered analytics provide deep visibility into network traffic and potential threats. This enables proactive threat detection and mitigation, minimizing risk within your environment.
Key Benefits
-
Enhanced Security Posture: Nile's Zero Trust model significantly reduces the likelihood and impact of successful cyberattacks.
-
Streamlined Operations: Granular segmentation simplifies policy management, improving operational efficiency.
-
Adaptable to New Threats: AI-driven analytics and dynamic policy integration provide agility in responding to emerging threats.
Learn more about Campus Zero Trust.
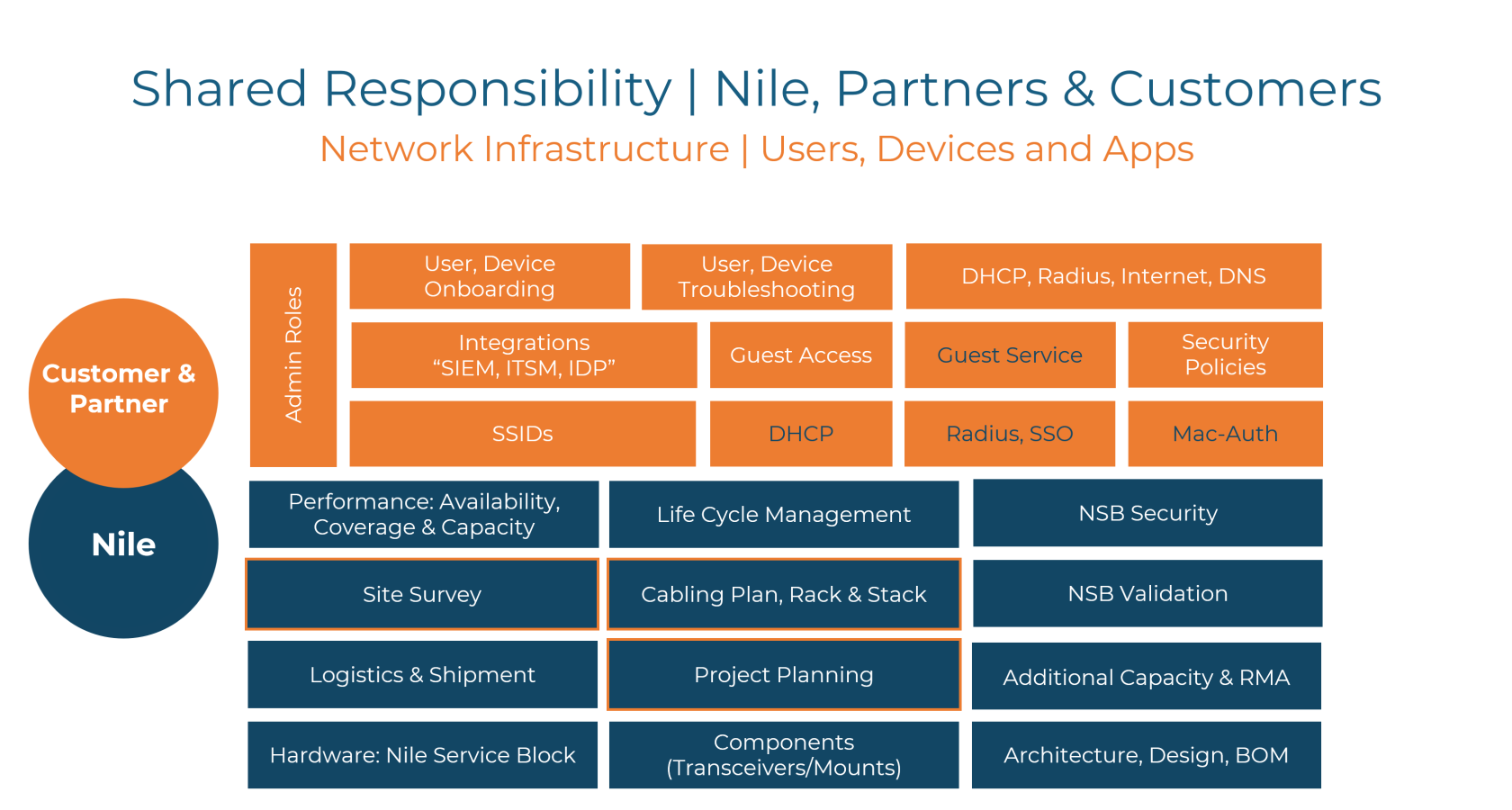
Shared Responsibility
Nile simplifies network operations by providing a cloud-delivered connectivity solution. This model ensures optimal network performance and security through a clear division of responsibilities.
Nile's Responsibilities:
- Connectivity Infrastructure: Design, deployment, and continuous operation of the Nile Service Block (switches, APs, sensors).
- Platform Management: All software updates, feature releases, and configuration of the Nile cloud-based management platform.
- Reliable Connectivity: Ensuring Nile components adhere to the strict SLAs, guaranteeing network availability, coverage, and capacity.
- Proactive Monitoring: 24/7 visibility into Nile service health, with proactive issue resolution ensuring an exceptional user experience.
Customer Responsibilities
- Network Strategy: Customers provision their intent on top of our standard system design across campus and branch locations. This includes management of upstream security appliances (firewalls), WAN connectivity, NAC/SASE solutions, and DHCP infrastructure.
- Endpoint Security: Security solutions and policies on end-user devices remain within the customer's domain.
Collaborative Support
Nile provides comprehensive support for the Nile Access Service. In scenarios where issues might require coordination between Nile infrastructure and customer-managed components, clear communication channels and escalation processes enable rapid troubleshooting and problem resolution.
RL -->Should we make a 3-tier RACI showing partner responsibility like showing site survey, Cabling, Rack, and Stack, RMA.
Also, DHCP is mentioned in two orange blocks. Why is Guest Access and Guest Service different? Guest Service is Nile-specific only.
In the graphic above an orange box (DHCP, DNS etc.) with blue text is an optional service, customers can use their own solutions.
Items in blue boxes with an orange border (Site Survey, Cabling plan, etc.) can be conducted by the customer or partner, adhering to Nile's established standards.
Our commitment to shared responsibility starts with planning your Nile Access Service deployment together using this framework.
Read Next
What is the Nile Architecture?
No Comments