Nile Access Service 802.1x
Overview
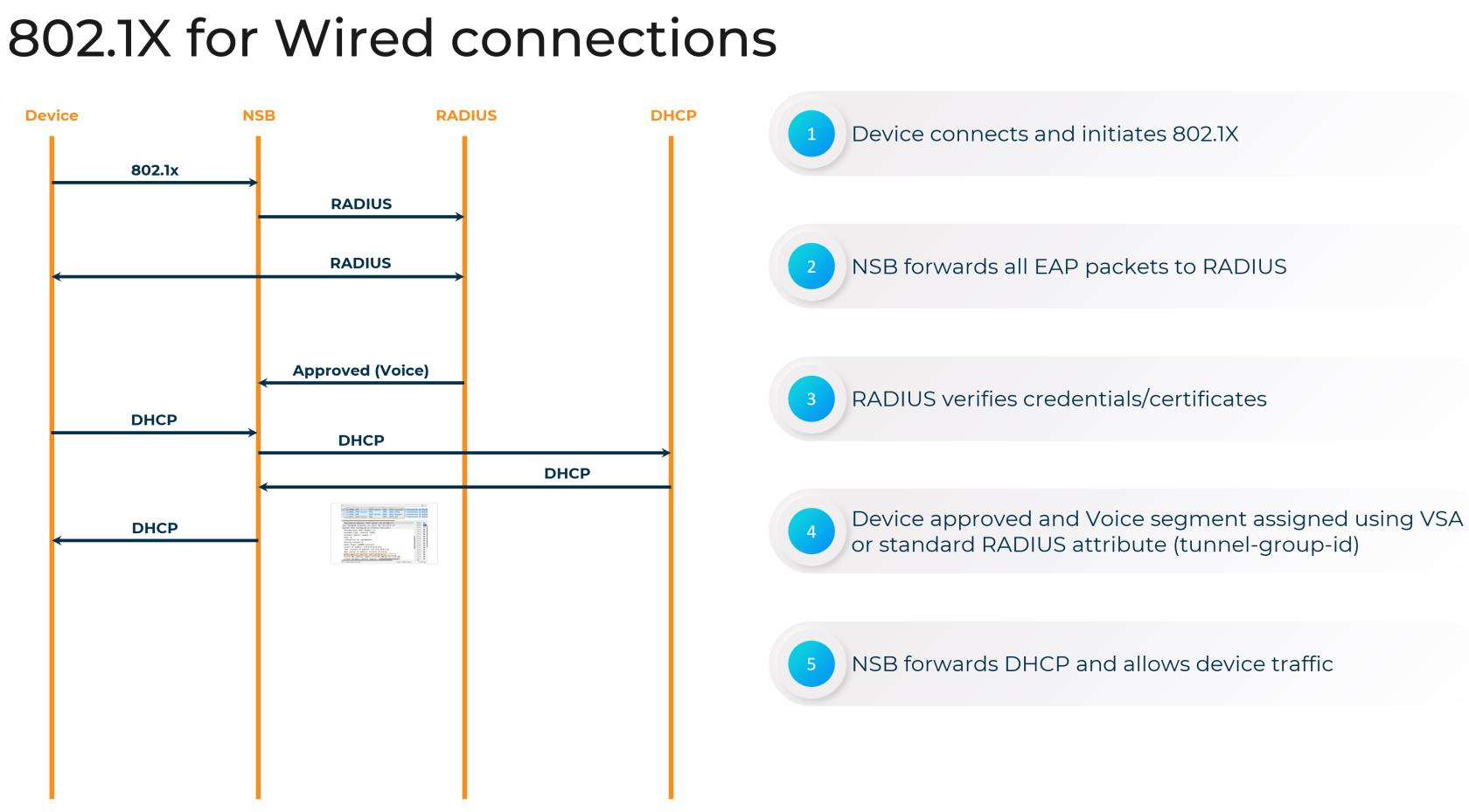
Nile's Campus Zero Trust approach to network security is essential in today's high risk environment. Nile's support for industry-standard 802.1X authentication enables you to enforce consistent access controls and policies across your wired and wireless campus networks, ensuring only authorized devices and users can connect.
By integrating with your existing RADIUS infrastructure, such as Active Directory, to authenticate clients The Nile Access Service ensures only authorized devices and users can access network resources. In the Campus Zero Trust architecture, devices are denied access by default, and can only access resources through one of the supporteed authentication methods, including 802.1x. This streamlines the onboarding process and ensures a seamless user experience, all while maintaining a strong security posture.
Shiv> I forgot about this. We need to upload the NIle dictionary file here. This file is uploaded in the RADIUS server and is used to send us back the segment name as a Vendor specific attribute.
Use Case: Single SSID for teacher and students
- Teacher belongs to teacher segment
- Student belongs to student segment
- The SSID Univ of Den is mapped to both teacher and student segment
- The RADIUS server has the dictionary file uploaded (I started a thread with Mak to get the latest file)
- The RADIUS server is configured to send netseg=teacher as part of the RADIUS response when a teacher successfully authenticates and netseg=student when a student authenticates
- The values that the RADIUS server sends should be an exact match (case sensitive) to the segments configured
- Optionally we can use the standard RADIUS attribute tunnel-id (Mak can confirm) instead of the dictionary file. So we need to document both methods
Also lets create a separate section for UPSK with External RADIUS (ISE/ClearPass)
Configuring 802.1X Authentication on Nile
To set up 802.1X authentication on your campus zero trust network with Nile, follow these steps:
-
Configure RADIUS Servers
- In the Nile Portal, navigate to "Settings>Authentication" tab and click "Add".
- Enter the details for your RADIUS server, including the Name, port, shared secret, the Geo Scope which it supports, nad the IP address or FQDN. I
- Click the "VERIFY HOSTS" button to confirm your settings. If everything passes, you can then save this server configuration.
-
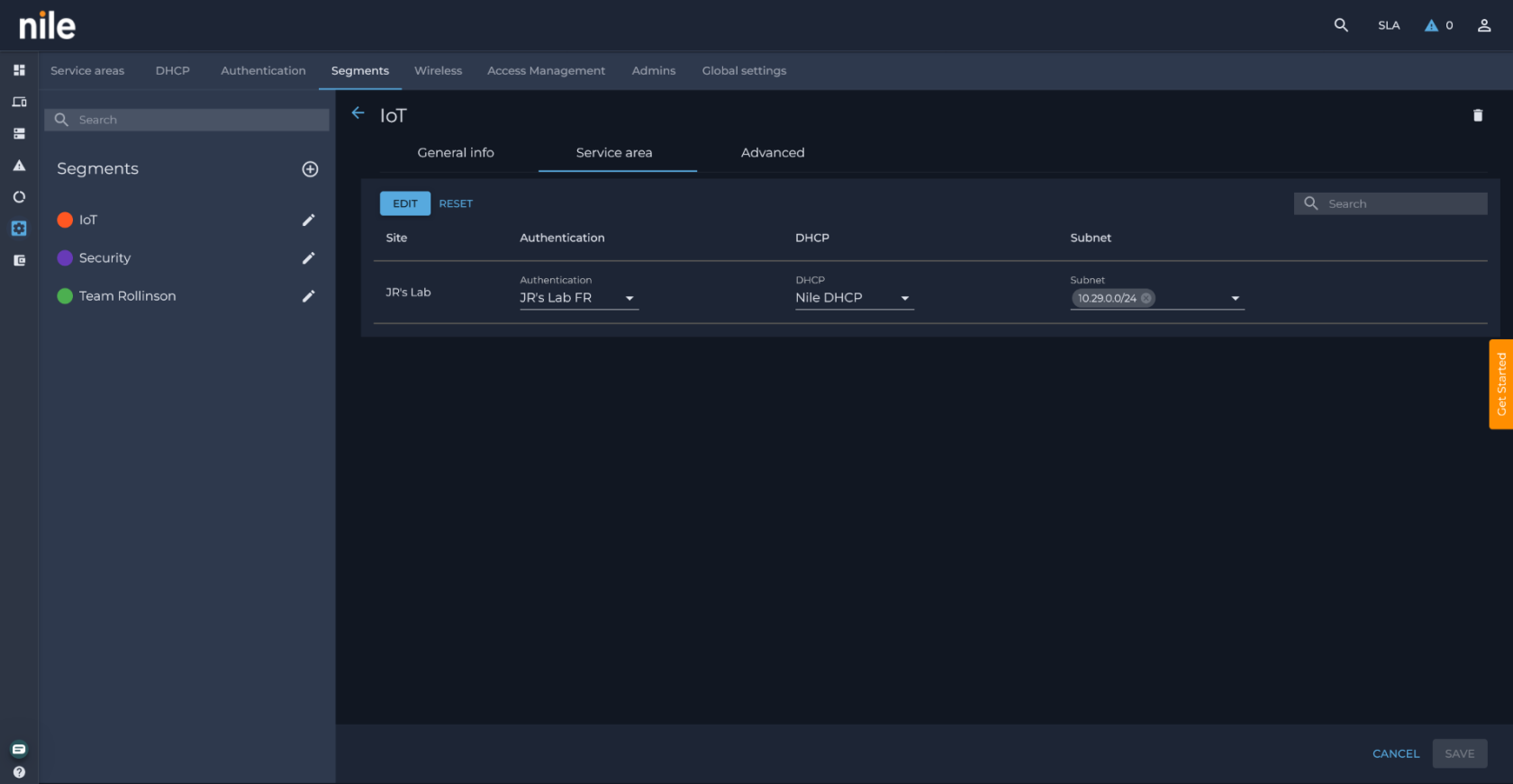
Enable 802.1X on a Nile Segment
- Go to Settings>Segements tab. section, click the pencil icon to edit your chosen segment.
- In the segment details, navigate to the Service Area tab.
- Select the RADIUS server you just configured in the Authentication dropdown.
- Click SAVE to immediately enable 802.1x on that segment.
Supporting Non-802.1X Devices in a Campus Zero Trust Network
Nile understands that not every device on your network will support 802.1X. For these non-802.1X-capable clients, Nile offers MAC Authentication Bypass; learn more.
Centralized Management and Visibility
Nile's cloud-managed architecture provides a simple path for 802.1X deployment. This includes the ability to:
- Easily onboard and manage multiple RADIUS servers for redundancy and segmentation
- Shiv> We should point out how redundancy works
- Its a primary, secondary, tertiary model. So only if primary faiils we send it to secondary and if secondary fails we send it to tertiary. I will find out what happens if primary comes online.
- Shiv> We should point out how redundancy works
- Track authentication events and client activity across your wired and wireless networks
- Quickly troubleshoot connectivity issues with detailed logs and reporting
(Screenshot of the Nile Portal's 802.1X monitoring and reporting dashboard)
By leveraging Nile's 802.1X capabilities, you can establish a robust, campus zero trust network that securely connects all devices and users, regardless of their location or device type.
Contact us today to learn more about how Nile can help secure your campus environment.