MAC Authentication Bypass (MAB)
MAB and the Zero Trust Campus
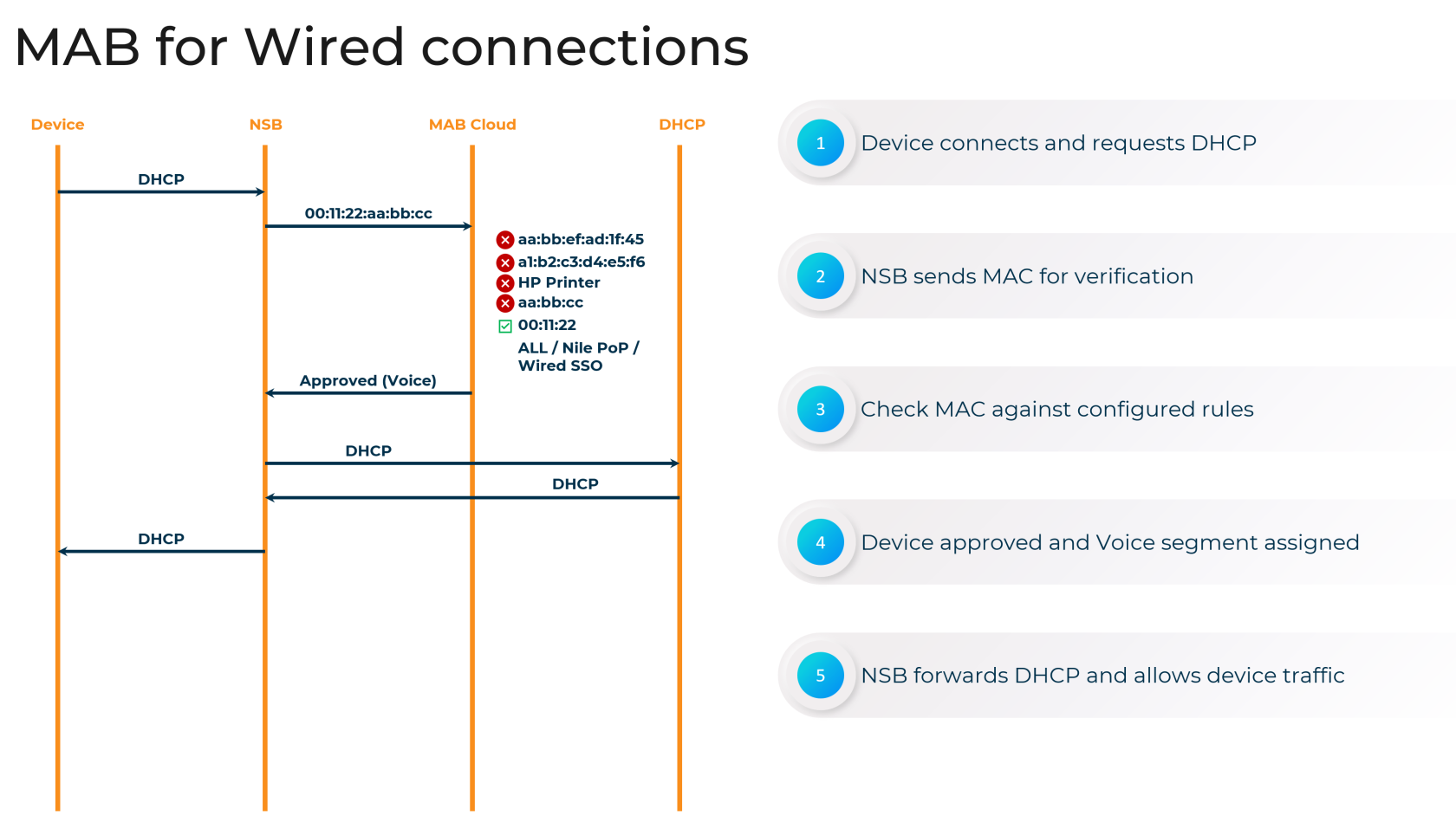
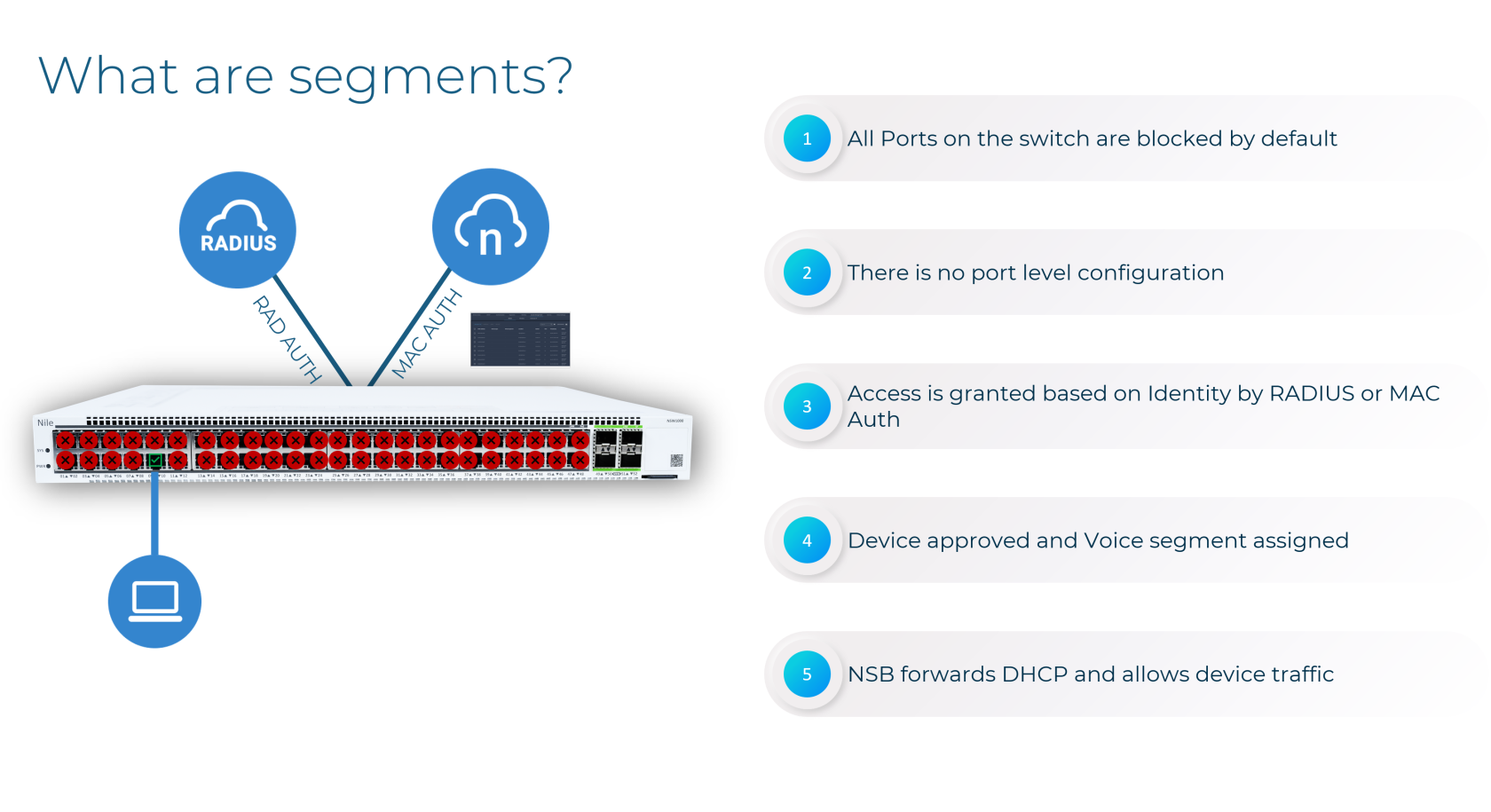
The Nile Access Service is built on the principles of a "Zero Trust Campus," ensuring that no user or device is implicitly trusted. As part of this security model, the Nile Access Service supports MAC Authentication Bypass (MAB) as an authentication method for devices that cannot accommodate the 802.1X standard.
While MAB provides network access for non-802.1X capable devices, such as printers and IoT equipment, it is essential to maintain the principles of Zero Trust. Nile's implementation of MAB includes additional security measures to isolate these devices and limit their potential impact on the network.
Why Use MAB?
Nile requires all wired access to be authenticated before granting network connectivity. The Nile Access Service supports three different wired authentication methods:
- Wired 802.1X authentication (requires a RADIUS server)
- Wired RADIUS MAB authentication (requires a RADIUS server)
- Nile Portal Wired MAB authentication
MAB is a crucial authentication method for devices that cannot support the 802.1X standard, ensuring comprehensive coverage and secure access to Nile Access Service Segments.
Configuring MAB
Nile provides flexible options for configuring MAB within the Nile Access Service:
Uploading a MAC Address List
You can upload a list of MAC addresses for wired MAB authentication by navigating to the Nile Portal (Settings > Access Management > Wired) and providing the following information:
- MAC address: The device's MAC address (mandatory)
- Segment: The network segment to which the device should be assigned (required for "Allow" status, optional for "Deny")
- Lock to Port: Lock the device to a specific switch port (optional)
- Site, Building, Floor: Restrict the device to a specific geographical location (optional)
- Allow or Deny: Specify whether to allow or deny access for the device (mandatory)
[screenshot required]
Enabling Auto-MAB for Specific Device Types
You can also configure Nile to automatically authenticate devices based on their Organizational Unique Identifier (OUI), the first 24 bits of a MAC address that identify the device manufacturer. This can be done in the Nile Portal (Settings > Access Management > Wired > Add Device > OUI/MAC), where you can select the segment, status (Approved/Denied), and geographical scope for the OUI-based policy.
[screenshot required]
MAB Port Locking and Geographical Scope
Nile offers additional security features for MAB, including the ability to "Lock to Port" and restrict devices to specific geographical locations ("Geo Scope"). These options help mitigate the risks associated with MAB by ensuring that devices can only connect to authorized switch ports and locations.
[screenshot required]
Disabling Nile Wired Authentication
Nile's network is designed with security best practices in mind, and you cannot disable MAB authentication entirely. However, you can create a catch-all "allow all" policy to grant network access to all devices, assigning them to a specific segment. While this approach is not recommended, it can be enabled in the Nile Portal (Settings > Access Management > Wired > Add Device > Allow all MACs).
Remember that the "allow all" policy will automatically create a unique MAC-allowed entry for each device when it first connects to the Nile switch. Deleting the "allow all" policy will not impact connected devices or delete the specific policies that were auto-created.
By understanding the role of MAB within the Nile Access Service and the available configuration options, you can ensure that non-802.1X capable devices are granted secure network access while maintaining the principles of the Zero Trust Campus.
Summary
In summary, the Nile Access Service's implementation of MAC Authentication Bypass (MAB) is a vital component of our comprehensive authentication framework. Nile's flexible MAB configuration options, including MAC address lists, auto-MAB for specific device types, and advanced security controls like port locking and geographical restrictions, empower organizations to extend secure network access to a wide range of devices, including those that cannot support 802.1X.
Furthermore, Nile's innovative approach to network segmentation, which transcends traditional VLAN-based models, enhances the benefits of MAB. The Nile Access Service's Layer 3 segmentation, driven by user identity, device attributes, and application requirements, enables granular access controls and micro-segmentation. This powerful combination of MAB and Nile's advanced segmentation strategy helps enterprises maintain a robust security posture while accommodating diverse connectivity needs, in alignment with Zero Trust principles.
By leveraging the flexibility and security of MAB within Nile's innovative network architecture, organizations can confidently provide secure access to a wide range of devices, minimizing the attack surface and reducing the risk of lateral movement. As a key part of the Nile Access Service's authentication framework, MAB contributes to the overall effectiveness of this cloud-native network solution in helping enterprises build resilient, agile, and highly secure network environments.
Nile Wired Access Management FAQ
Why do we need Wired Access Management?
Nile requires all wired devices to be authenticated before accessing the network, Nile
supports three different Wired authentication methods:
1- Wired 802.1x authentication (required RADIUS)
2- Wired MAC-Auth authentication (required RADIUS)
3- Nile Portal Wired Access management authentication
Can I upload a list of Wired pre-approved devices to Access Management
authentication?
Yes, You can upload a list of the pre-approved devices to Access Management by
uploading CSV file via Nile Portal (Settings -> Access management-> Wired)
“MAC address” devices MAC address, this field is mandatory.
"Segment" will be the segment name you assign the Wired device to, the
segment must match an existing segment, this field required only for “Allow”
status and optional for “Deny”
“Lock to Port” lock the device to a specific switch/port when it first connects to
Nile Network, this field is optional
"Site" allows the device to authenticate/connect in a specific site only this field is
optional.
"Building" allows the device to authenticate/connect in a specific site/building
only this field is optional.
"Floor" allows the device to authenticate/connect in a specific site/building/floor
only this field is optional.
“Allow or Deny” to allow or deny specific devices based on MAC address, this
field is mandatory.
Can I Disable Nile Wired Device Authentication?
Nile network is designed with security best practices, you cannot disable
wired device authentication, but you can add a catch-all auto policy (not
recommended) to allow all devices and assign them to a specific segment.
You can enable the allow-all policy via Nile portal from (Settings -> Access
management-> Wired -> ADD DEVICE -> Allow all MACs, and select the
default segment for all new devices)
Allow all MACs policy will automatically create a unique MAC-allowed
entry for each device when the device connects to the Nile switch for the
first, deleting the “Allow all MACs” policy will not impact connected devices
or delete a specific policy that is auto-created by all policy.
Can I Enable Nile Auto Wired Device Authentication for a Specific Vendor Or
Device type?
You can create a wired device authentication policy for a specific device
vendor or type using OUI, OUI is the first 24 bits of a MAC that is used as a
globally unique identifier assigned by the Institute of Electrical and
Electronics Engineers (IEEE) to identify network devices.
You can enable the OUI via Nile portal from (Settings -> Access
management-> Wired -> ADD DEVICE -> OUI/MAC , select a segment for
the new devices, status (Approved/Denied), and Geo Scope )
OUI MACs policy will automatically create a unique MAC-allowed entry for
each device when the device connects to the Nile switch for the first time,
deleting the “OUI MACs” policy will not impact connected devices or delete
a specific policy that is auto-created by OUI policy.
What is Nile Wired Access Management Lock to port?
Port Lock will lock device approval to a specific Nile switch/port when the
device connects for the first time, moving the wired device to a different
port or different switch, Wired Access Management policy will be changed
from allow to deny, Nile portal admin will need to allow the device again.
To enable Port lock for specific device or devices, you can enable it via
Nile portal (Settings -> Access management-> Wired -> ADD DEVICE ->
enable Lock to port, enter OUI (for multi devices) or MAC (for single
device), select a specific segment, optional you can select Geo scope to
allow the device to be connected in a specific location)
What is Wired Access Management Geo scope?
Wired Access Management Geo scope is to limit wired device
authentication pre-approval to a specific location (specific site or building or
floor), moving the wired device to a different location, Wired Access
Management policy will be changed from allow to deny, Nile portal admin
will need to allowed the device again
To enable Geo Scope for a specific device or devices, you can enable it via
Nile portal (Settings -> Access management-> Wired -> ADD DEVICE ->,
enter OUI (for multi devices) or MAC (for a single device), select a specific
segment, select Geo scope (Site or Building or Floor, or multi-location) to
pre-approved the device to be connected on a specific location
Can admin pre-approve devices based on the make and model of devices or
device software example an Avaya IP Phone or MS Windows 10 PC?
Nile can fingerprint devices and allows admins to create fingerprint-based rules to
pre-approve devices. You can navigate to Settings → Access Management →
Wired → Add Devices. Nile has an exhaustive list of device models, make and
OS that can be leveraged to create rules. When you start typing the name of your
device we will auto-populate and display the matches in our database
What happens if my device is not on the list?
If your device is not on the list, the admin will have to leverage the MAC address
or OUI for pre-approval. They can reach out to Nile and provide details of the
device so it can be reviewed and added at a later date.
How does Fingerprint-based approval work?
A. When a new device is plugged into the network following is the order of match:
1. The exact MAC address rule match always wins
2. Fingerprint rule match.
3. OUI rule match
4. All rule match.
When a new device does not match an exact MAC address, it will be matched
against a fingerprint rule. As the device will not have an IP address, we have limited
information like MAC address to fingerprint. To have the device get a temporary IP
you need to create an ALL rule with a quarantine or Internet-only segment. Our
fingerprinting uses MAC, DHCP and DNS transactions, and User-agent data as some
of the parameters to get an accurate match. So, if the device does not match the
fingerprint rule, it will go to the segment defined in the ALL rule. Once it gets a
temporary IP and starts doing some transactions, it will get fingerprinted and
automatically moved to the fingerprint segment, the device IP address will be
changed from the new segment. Nile will learn the device fingerprint and create a
specific entry for the future.
If I create an exact MAC address entry of the device with segment A, will the
device be moved to fingerprint segment B once fingerprinted?
Nile will only move devices automatically if they match the ALL rule. Devices
matching an exact address or OUI will not be moved automatically. Thus it is
recommended to not create exact MAC addresses or OUI entries for devices that
you want to onboard using fingerprinting
What happens if Nile fingerprints a device incorrectly?
If a device is fingerprinted incorrectly, Nile recommends removing the device from
the cache (we are adding this as an enhancement) and adding the exact MAC
address. They can contact Nile and provide the details so we can evaluate and
add them to our database in the future.
What happens if a device matches two fingerprint rules?
When two rules match the most specific one wins. So Avaya IP Phone 250 will
win over Avaya.
I connected my wired devices and then created rules (Fingerprint or OUI or ALL
rules), all my devices are still waiting for approval.
Rules need to be created before connecting the devices, when the device
connects, Wired Access Management matches existing rules, if there are no rules
match, device entry will be created with waiting for approval status, to have a new
rule applied, we will need to delete device entry and disconnect/connect the
device to apply the new rule, Nile adding an enhancement to verify all existing
entries with waiting for approval status after creating a new rule, if the device with
waiting for approval match, the status will auto change to allow/deny based on the
new rule.
What happens if we delete an existing rule?
Deleting an existing rule will not impact any existing device Wired Access
Management entry, it will only impact adding new devices, when a device is
added, if it matches a rule, it will create a specific entry for the device, only impact
if both the rule and device entry got deleted, in this case, the device status will
change to waiting for approval and required a manual approval.