MAC Authentication Bypass (MAB)
MAB and the Zero Trust Campus
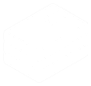
The Nile Access Service is built on the principles of a "Zero Trust Campus," ensuring that no user or device is implicitly trusted. As part of this security model, the Nile Access Service supports MAC Authentication Bypass (MAB) as an authentication method for devices that cannot accommodate the 802.1X standard.
While MAB provides network access for non-802.1X capable devices, such as printers and IoT equipment, it is essential to maintain the principles of Zero Trust. Nile's implementation of MAB includes additional security measures to isolate these devices and limit their potential impact on the network.
Why Use MAB?
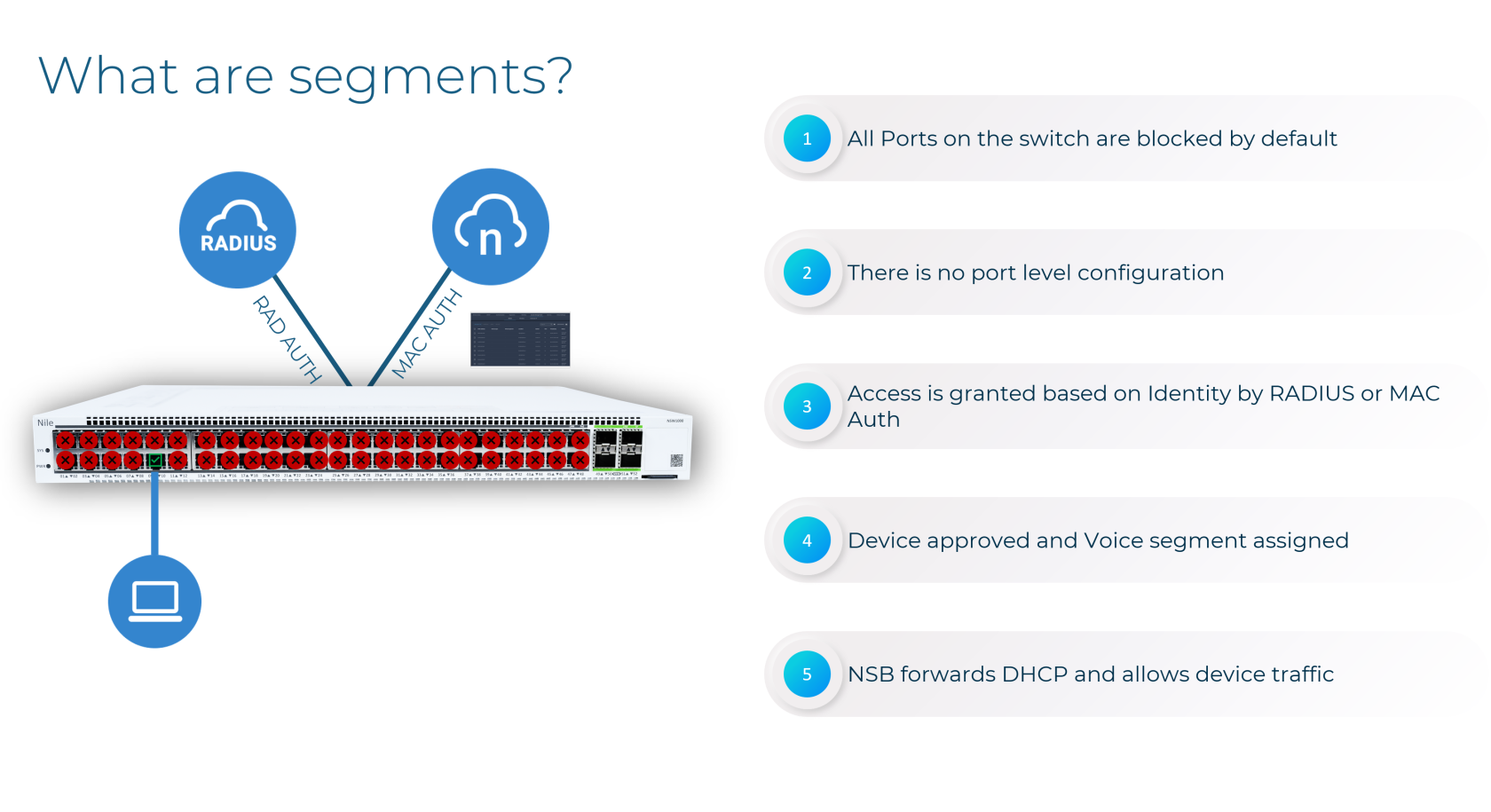
Nile requires all wired access to be authenticated before granting network connectivity. The Nile Access Service supports three different wired authentication methods:
- Wired 802.1X authentication (requires a RADIUS server)
- Wired RADIUS MAB authentication (requires a RADIUS server)
- Nile Portal Wired MAB authentication
MAB is a crucial authentication method for devices that cannot support the 802.1X standard, ensuring comprehensive coverage and secure access to Nile Access Service Segments.
Configuring MAB
Nile provides flexible options for configuring MAB within the Nile Access Service:
Uploading a MAC Address List
You can upload a list of MAC addresses for wired MAB authentication by navigating to the Nile Portal (Settings > Access Management > Wired) and providing the following information:
- MAC address: The device's MAC address (mandatory)
- Segment: The network segment to which the device should be assigned (required for "Allow" status, optional for "Deny")
- Lock to Port: Lock the device to a specific switch port (optional)
- Site, Building, Floor: Restrict the device to a specific geographical location (optional)
- Allow or Deny: Specify whether to allow or deny access for the device (mandatory)
[screenshot required]
Enabling Auto-MAB for Specific Device Types
You can also configure Nile to automatically authenticate devices based on their Organizational Unique Identifier (OUI), the first 24 bits of a MAC address that identify the device manufacturer. This can be done in the Nile Portal (Settings > Access Management > Wired > Add Device > OUI/MAC), where you can select the segment, status (Approved/Denied), and geographical scope for the OUI-based policy.
[screenshot required]
MAB Port Locking and Geographical Scope
Nile offers additional security features for MAB, including the ability to "Lock to Port" and restrict devices to specific geographical locations ("Geo Scope"). These options help mitigate the risks associated with MAB by ensuring that devices can only connect to authorized switch ports and locations.
[screenshot required]
Disabling Nile Wired Authentication
Nile's network is designed with security best practices in mind, and you cannot disable MAB authentication entirely. However, you can create a catch-all "allow all" policy to grant network access to all devices, assigning them to a specific segment. While this approach is not recommended, it can be enabled in the Nile Portal (Settings > Access Management > Wired > Add Device > Allow all MACs).
Remember that the "allow all" policy will automatically create a unique MAC-allowed entry for each device when it first connects to the Nile switch. Deleting the "allow all" policy will not impact connected devices or delete the specific policies that were auto-created.
By understanding the role of MAB within the Nile Access Service and the available configuration options, you can ensure that non-802.1X capable devices are granted secure network access while maintaining the principles of the Zero Trust Campus.
Summary
In summary, the Nile Access Service's implementation of MAC Authentication Bypass (MAB) is a vital component of our comprehensive authentication framework. Nile's flexible MAB configuration options, including MAC address lists, auto-MAB for specific device types, and advanced security controls like port locking and geographical restrictions, empower organizations to extend secure network access to a wide range of devices, including those that cannot support 802.1X.
Furthermore, Nile's innovative approach to network segmentation, which transcends traditional VLAN-based models, enhances the benefits of MAB. The Nile Access Service's Layer 3 segmentation, driven by user identity, device attributes, and application requirements, enables granular access controls and micro-segmentation. This powerful combination of MAB and Nile's advanced segmentation strategy helps enterprises maintain a robust security posture while accommodating diverse connectivity needs, in alignment with Zero Trust principles.
By leveraging the flexibility and security of MAB within Nile's innovative network architecture, organizations can confidently provide secure access to a wide range of devices, minimizing the attack surface and reducing the risk of lateral movement. As a key part of the Nile Access Service's authentication framework, MAB contributes to the overall effectiveness of this cloud-native network solution in helping enterprises build resilient, agile, and highly secure network environments.
Nile requires all wired devices to be authenticated before accessing the Nile Wired Access Management FAQ
Why do we need Wired Access Management?
network,network. The Nile
Access Service supports three different Wiredwired authentication methods:1-
- Wired 802.
1x1X authentication (requiredrequiresRADIUS)2-a RADIUS server) - Wired
MAC-AuthRADIUS MAB authentication (requiredrequiresRADIUS)3-a RADIUS server) - Nile Portal Wired Access management authentication
Can I upload a list of Wired pre-approved devices to Access Management
authentication?Management?
Yes, Youyou can upload a list of the pre-approved devices to the Nile Access Management by
uploading a CSV file via the Nile Customer Portal (Settings ->> Access management->Management > Wired)“. The CSV file should include the following information:
- MAC
address”address:devicesThe device's MACaddress,addressthis(mandatory) - Segment:
isThemandatory."Segment"network segment the device will betheassignedsegmenttoname you assign the Wired device to, thesegment must match an existing segment, this field(requiredonlyfor“Allow”status"Allow"andstatus, optional for“Deny”“"Deny") - Lock to
Port”Port:lockLock the device to a specificswitch/switch portwhen(optional) - Site,
firstBuilding,connectsFloor:toNile Network, this field is optional"Site" allowsRestrict the device toauthenticate/connect ina specificsitegeographicalonlylocationthis(optional) - Allow or
Deny”Deny: Specify whether to allow or denyspecificaccessdevicesforbasedtheondeviceMAC(mandatory)
Can I Disable Nile Wired Device Authentication?
No, the Nile network is designed with security best practices, and you cannot disable
wired device authentication,authentication butentirely. However, you can add a catch-all auto"allow all" policy (not
recommended) to allowgrant network access to all devicesdevices, and assignassigning them to a specific segment.You This policy can enablebe enabled in the allow-all policy via Nile portalCustomer fromPortal (Settings ->> Accessmanagement-> Management > Wired ->> ADDAdd DEVICEDevice ->> Allow all MACs,MACs).
Can I Enable Nile Auto Wired Device Authentication for a Specific Vendor Or
or Device
Yes, you can create a wired device authentication policy for a specific device
vendor or type using
globally unique identifier assigned by the
You can enable the
the
What is Nile Wired Access Management Lock to port?
The "Lock to Port" feature will lock devicea device's approval to a specific Nile switch/switch port when the
device connects for the first
port or a different switch, the Wired Access Management policy will be changed
from
"Lock to Port" feature in the Nile
Wired Access Management Geo scope is to limit wired deviceauthentication pre-approval to a specific location (specific site or building orfloor), moving the wired device to a different location, Wired AccessManagement policy will be changed from allow to deny, Nile portal adminwill need to allowed the device againTo enable Geo Scope for a specific device or devices, you can enable it viaNile portal (Settings -> Access management-> Wired -> ADD DEVICE ->,enter OUI (for multimultiple devices) or MAC (for a single device), selectselecting a specific
segment, selectand optionally choosing the geographical scope.
What is Wired Access Management Geo scopeScope?
The orWired BuildingAccess orManagement Floor,Geo orScope multi-location)is topre-approveda thefeature that limits wired device authentication pre-approval to be connected on a specific location (site, building, or floor). If a wired device is moved to a different location, the Wired Access Management policy will be changed from "allow" to "deny", and the Nile portal administrator will need to allow the device again.
You can enable the Geo Scope in the Nile Customer Portal (Settings > Access Management > Wired > Add Device) by entering the OUI (for multiple devices) or MAC (for a single device), selecting a specific segment, and choosing the geographical scope (site, building, or floor).
Can adminAdministrators pre-approvePre-Approve devicesDevices basedBased on theDevice makeMake, and model of devices or
device software example an Avaya IP PhoneModel, or MSSoftware?
Yes, 10the PC?
Nile Access Service can fingerprint devices and allows adminsadministrators to create fingerprint-based rules to
pre-approve devices. You can navigate to "Settings →> Access Management →
> Wired →> Add Devices.Devices" in the Nile Customer Portal. Nile has an exhaustiveextensive listdatabase of device models, makemakes, andOS operating systems that can be leveragedused to create these rules. When you start typing the name of yourdevice wedevice, the system will auto-populate and display the matchesmatching entries in our database
database.
What happensIf ifMy my deviceDevice is notNot onin theNile's list?
Database?
If your device is not onin the list,Nile database, the adminadministrator will haveneed to leverageuse the MAC address
or OUIOrganizational Unique Identifier (OUI) for pre-approval. TheyYou can reach out to Nile support and provide the details of thedeviceyour device, so it can be reviewed and added to the database at a later date.
How doesDoes Fingerprint-basedBased approvalApproval work?
A.Work?
Nile's device isfingerprinting pluggedworks intoas thefollows:
- The exact MAC address rule match always
wins - If there is no exact MAC address match, the device will be matched against a fingerprint rule.
- If there is no fingerprint rule
match. - If
Allthererulearematch.
no other matching rules, the device will be assigned to the "All" rule.
When a new device doesconnects not match an exact MAC address, it will be matchedagainst a fingerprint rule. Asto the devicenetwork willand does not have an IP address, weNile havewill use limited
information like the MAC address to fingerprint.attempt a fingerprint match. To haveget the device get a temporary IP
address, you need to create an ALL"All" rule with a quarantine or Internet-only segment. Our
Nile's fingerprinting uses MAC,parameters DHCPlike andMAC address, DHCP, DNS transactions, and User-agentAgent data asto someofaccurately match the parametersdevice.
If the device does not match the
fingerprint rule, it will gobe toplaced in the segment defined inby the ALL"All" rule. Once itthe device gets a
temporary IP and starts doingcommunicating, someNile transactions,will fingerprint it willand get fingerprinted and
automatically movedmove it to the fingerprintcorrect fingerprint-based segment, updating the devicedevice's IP address will be
changed from the new segment.accordingly. Nile will learn the devicedevice's fingerprint and create a
specific entry for theit future.
going forward.
What Happens If I Create an Exact MAC Address Entry for a Device?
If you create an exact MAC address entry offor thea device with segmenta A, will thedevice be moved to fingerprintspecific segment Bassignment, once fingerprinted?
Nile will onlynot automatically move devicesthat automaticallydevice ifto theya matchdifferent thesegment ALLbased rule.on fingerprinting. Devices
matching an exact address or OUI rule will not be moved automatically. Thus itIt is
recommended not to not create exact MAC addressesaddress or OUI entries for devices that
you want to onboard using fingerprinting
fingerprinting.
What happens ifIf Nile fingerprintsFingerprints a deviceDevice incorrectly?
Incorrectly?
If a device is fingerprinted incorrectly, Nile recommends removing the device from
the cache (we are adding this as an enhancement) and adding the exact MAC
address. TheyYou can then contact Nile andsupport to provide the detailsdevice details, so we can evaluate and
add themit to our databasedatabase.
What happensHappens ifIf a Device Matches Multiple Fingerprint Rules?
When a device matches twomultiple fingerprint rules?
win over
a more general "Avaya" rule.
What If I connectedCreate myNew wiredRules devicesAfter andDevices thenAre createdAlready rulesConnected?
Rules need to be created before connecting the devices,devices. whenWhen thea device
connects, Wired Access Management
rule
device to apply the new
Nile is adding an enhancement to automatically verify all existing
entries with a "waiting for
new rule.
What happensHappens ifIf weWe deleteDelete an existingExisting rule?
Rule?
Deleting an existing rule will not impact any existing device Wired Access
Management
added, if it matches a rule,
would be if both the rule and the device entry
change to "waiting for